Axonius for CTEM: From scoping to prioritization

Editor’s note: The article below is adapted from our guide, Axonius for CTEM. You can view the full guide online for free here. |
Continuous Threat Exposure Management (CTEM) is a strategic approach to discovering and managing cyber risks, offering a pragmatic, always-on path to identifying, prioritizing, and mitigating threats.
We’ve covered the fundamentals before (see our intro to CTEM here), but now it’s time to roll up our sleeves.
In this excerpt from our full guide, Axonius for CTEM, we break down how to put CTEM into action with the Axonius Asset Cloud — helping you scope, discover, and prioritize exposures across your entire infrastructure.
CTEM step 1: Scoping
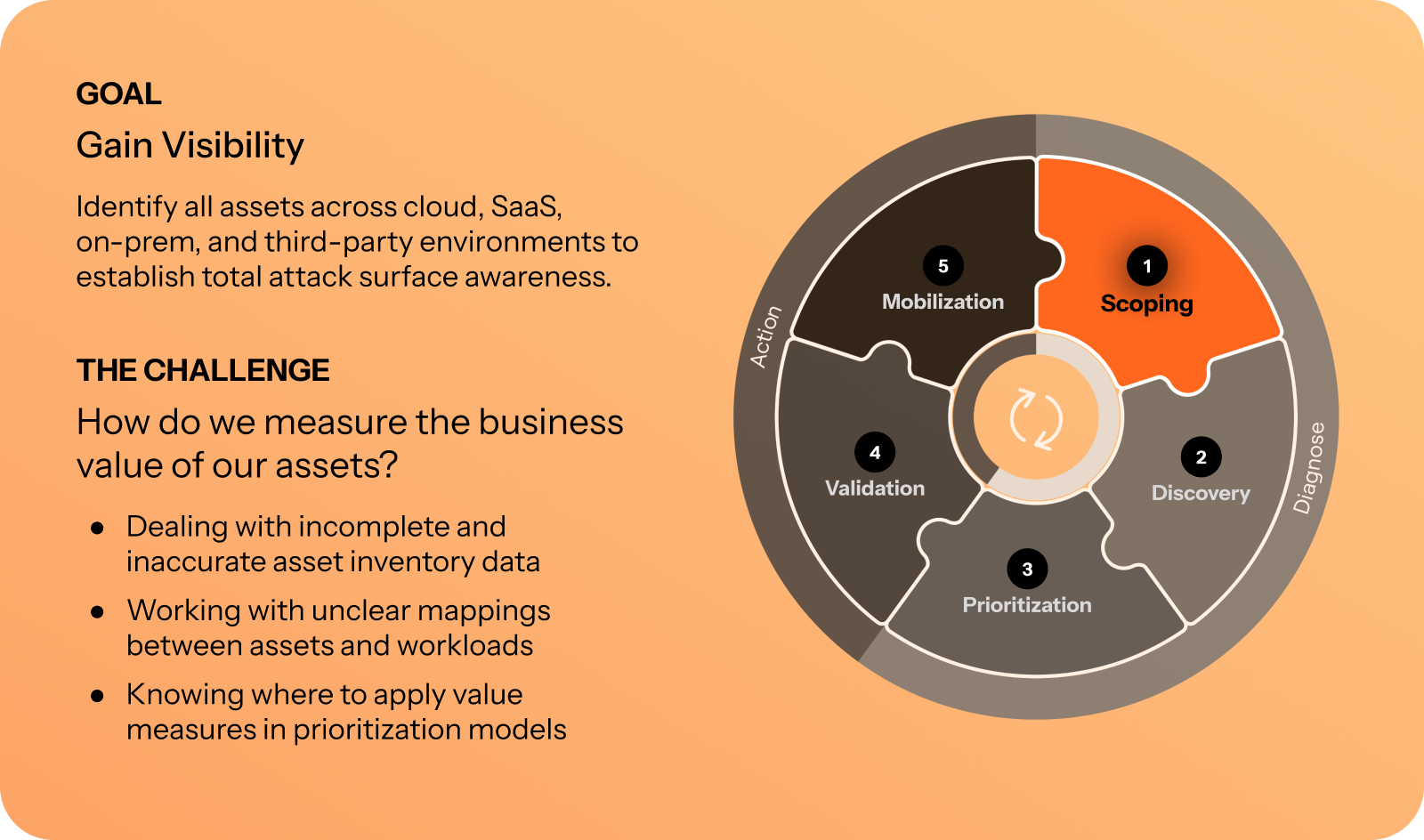
Scoping with Axonius
Axonius supports scoping by identifying all assets interfacing with your data and processes. We achieve scoping through adapters, discovery logic, and continuous discovery.
Adapters
To identify assets, Axonius integrates with your IT, Security, and business solutions using pre-built integrations known as adapters. As of June 2025, Axonius supports over 1,200 native adapters capable of identifying over 40 asset types regardless of where they are hosted.
Adapters are integrated using native and open APIs, eliminating the need for agents or network
tapping that introduces deployment friction, maintenance burden, and limitations in identifying shadow IT or assets outside your network.
Discovery logic
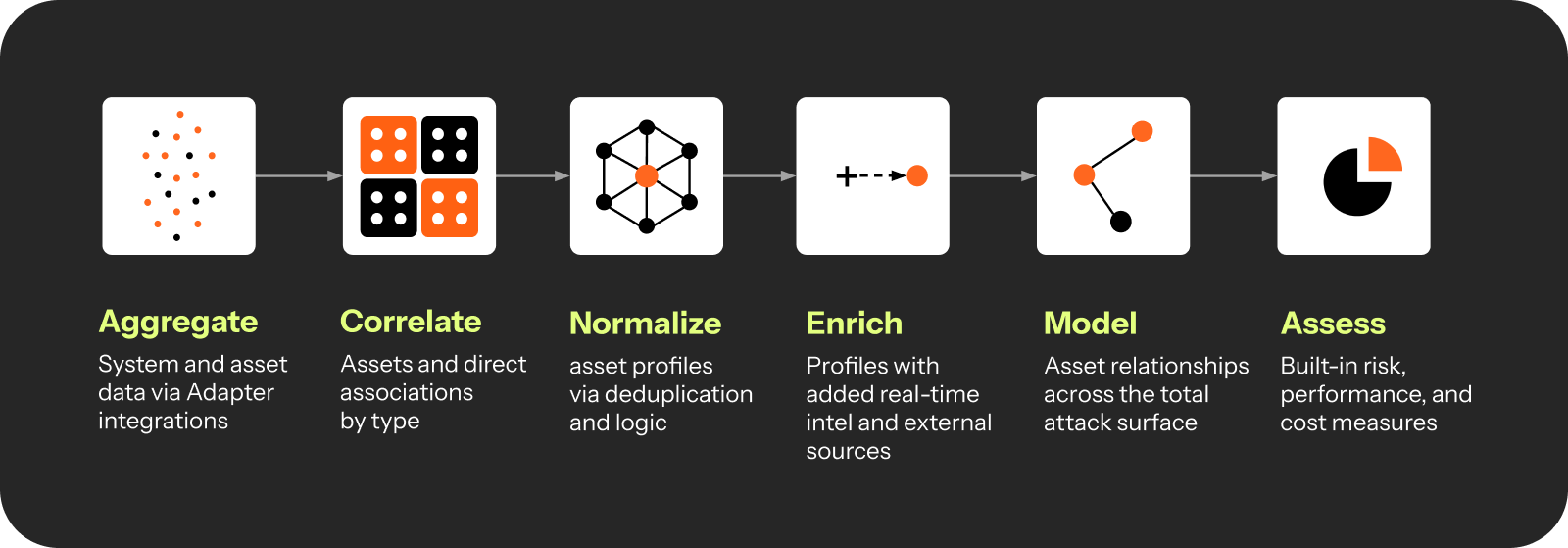
After collecting asset information, Axonius initiates its mapping phase (aggregation, correlation,
deduplication, normalization, and enrichment) to ensure your asset scoping is both complete and accurate, with assets uniquely identified, enriched, and free from inconsistencies.
The logic also sets the foundation for future steps in the CTEM process, like discovery.
For example:
By identifying a laptop under management accessing your internal applications, but missing your endpoint protection (EPP), you identify a blind spot in coverage.
CTEM step 2: Discovery
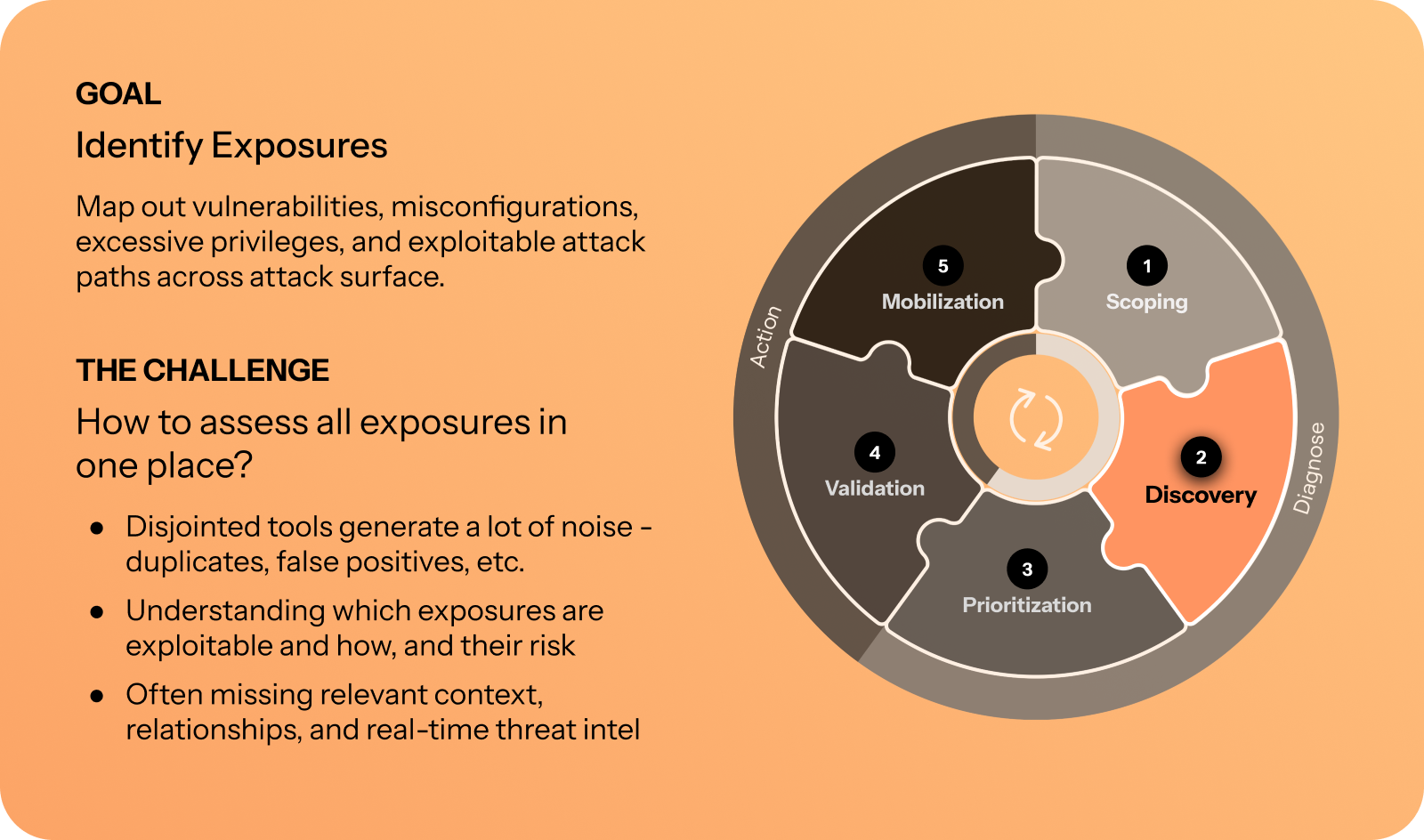
Axonius supports discovery by providing a single source of truth for exposures. The source of truth contains exposures reported by all your security tools alongside exposures identified by Axonius.
Axonius achieves discovery through exposure and vulnerability adapters, discovery logic, static analysis and enrichments, exposures, misconfigurations (through queries and dashboards), and external to internal mapping.
Discovery logic
Axonius leverages the same discovery logic from scoping assets to aggregate, correlate, and deduplicate your exposures. That gives your teams an accurate list of exposures that are uniquely identified, enriched, and free from inconsistencies.
Exposures
Axonius aggregate exposures — from all your assets across on-prem and cloud infrastructure — under the exposures category.
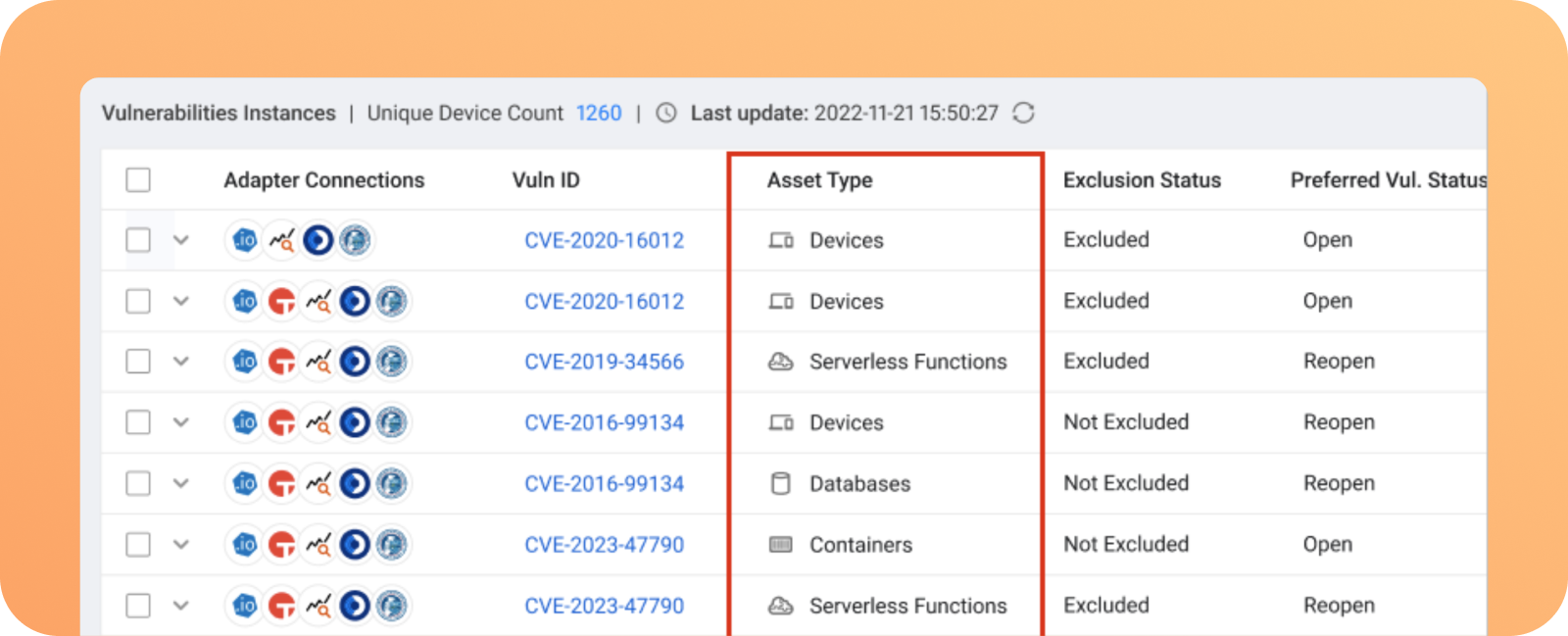
Each exposure item combines the security context (i.e. vulnerability CVE, technical score, threat intelligence feed data) with asset context and business context. This information is used in subsequent CTEM steps to help prioritize and mobilize the right teams.
CTEM step 3: Prioritization
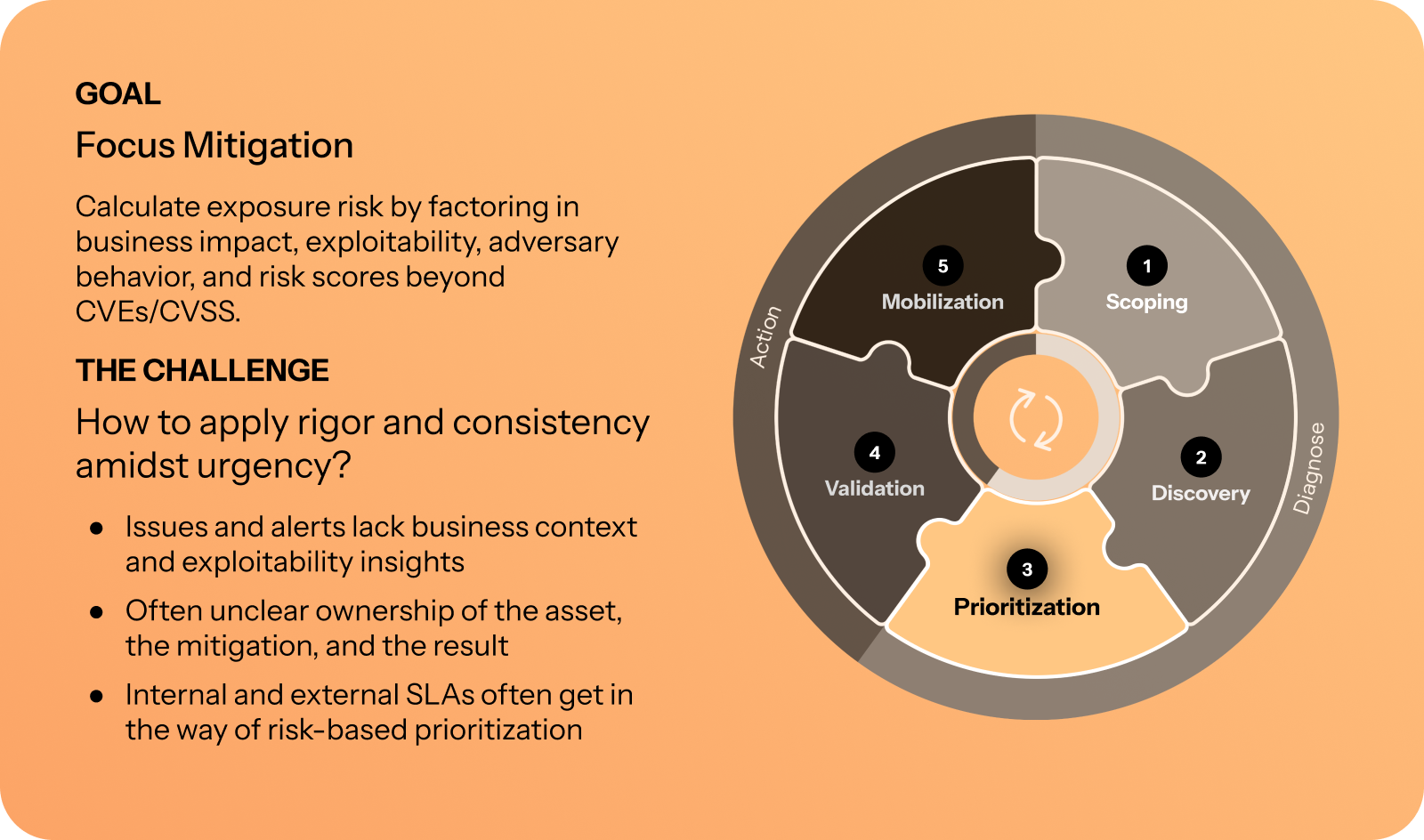
Prioritization with Axonius
Axonius supports prioritization by calculating the risk of your assets and exposures based on the security context (i.e. vulnerability CVE, technical score, threat intelligence feed data), asset context (i.e. asset state, status, and gaps), and business context (i.e. risk/business owner of the asset, crown jewel, in production, part of the PCI network).
Axonius achieves prioritization through its unified context, risk score engine, and dashboards.
Unified context
During Scoping and Discovery, Axonius collects and tracks the security context, asset context, and business context reported by your systems.
This information is combined, correlated, and made available for every asset and exposure in the Axonius platform, making the unified context available for prioritization decisions across all components — including queries, risk engine, dashboards, workflows, and automations.
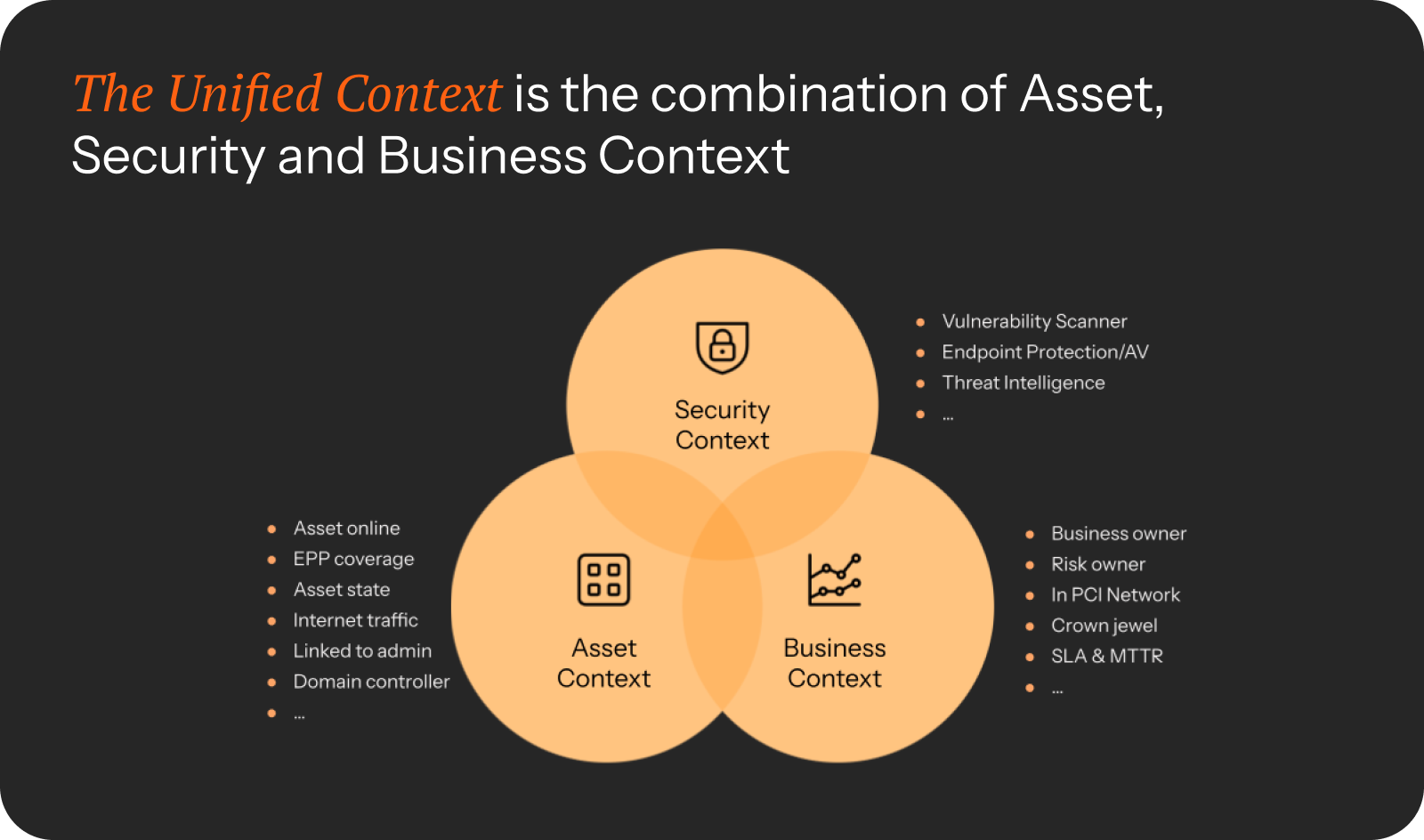
Example:
Unified Context used in the platform:
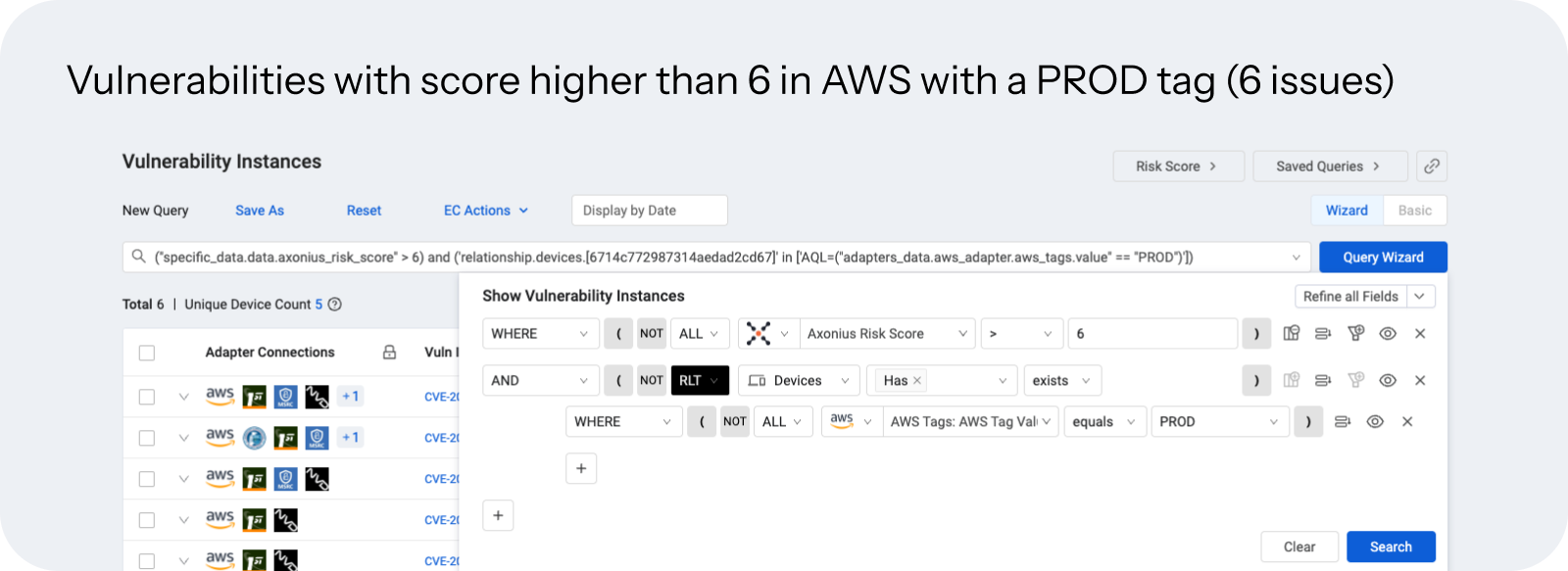
Risk score engine
The risk score engine quantifies the risk of assets and exposures based on the unified context. To calculate risk, organizations can either start from the Axonius-defined risk score or use their own logic based on their business characteristics.
The risk score helps organizations focus on exposures that require immediate attention and can also be used in subsequent steps to prioritize what exposures should go through validation and mobilization.
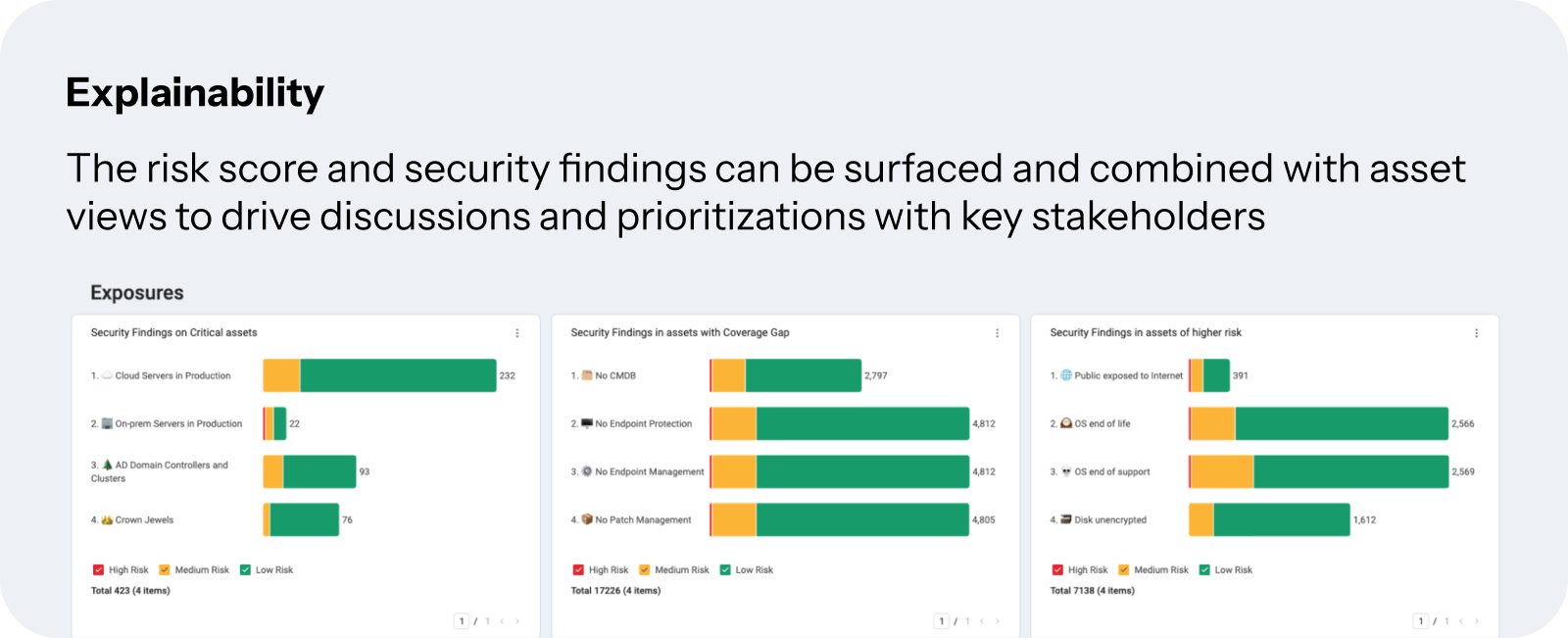
Dashboards
Dashboards leverage unified context and risk scores to surface CTEM prioritization in different ways. Dashboards are also used in subsequent steps to track the validation and mobilization of prioritized exposures.
Stop planning. Start doing CTEM.
Download our Axonius for CTEM eBook and learn how to:
Navigate the five core stages of a CTEM program: scoping, discovery, prioritization, validation, and mobilization
Configure the Axonius platform to support CTEM across your entire environment
Launch your program with quick wins, meaningful momentum, and continuous improvement
Already feeling inspired? Get a product demo or talk to our team and see how Axonius can help you put CTEM into action.
Categories
- Threats & Vulnerabilities
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
