How to Detect Gaps in Endpoint Protection with Axonius
Axonius

If you're responsible for endpoint coverage, you know how complicated it is to answer what should be a simple question:
Which devices are missing agents, and which have agents that aren’t working properly?
The data’s there. It’s just buried in too many places. Spread across tools, siloed in vendor consoles, and stale the moment you export it. That’s how blind spots happen. And it’s why policies meant to protect your environment often go unenforced.
Here’s a practical, step-by-step approach to using Axonius to find those gaps and close them fast.
Watch James Flores walk through how to detect gaps in endpoint protection. Keep reading for a full breakdown.
Step 1: Get the full picture of your environment
Before you can find what’s missing, you need to know what’s there. Axonius connects to 1,200+ security and IT tools to automatically build a complete, always up-to-date asset inventory. The platform pulls data on devices, users, applications, cloud instances, and more from across your environment, no matter where these assets live: on-prem, in remote networks, or across public and private clouds.
By correlating data across all of your systems, you’re not limited to one tool’s view of the world. You get full context, so you can identify missing or nonfunctioning agents and take action directly from the same view.

Axonius consolidates asset data across your environment into an always-up-to-date inventory, built to drive insights and action.
With complete visibility and no information silos, uncovering and closing security gaps becomes the easy part.
Step 2: Find devices missing a required endpoint agent
Let’s say your security policy states that all Windows machines must have CrowdStrike installed. The goal here isn’t to see which devices have the agent (your EDR console can tell you that). We want to identify devices that should have the agent but don’t. Here’s how to do it in Axonius.
Using the Query Wizard:
Filter for OS: Type equals Windows
Add a condition where CrowdStrike Agent ID does not exist
This query will surface all Windows devices that are missing the required agent, even if that device is known only to AD, a config tool, or another adapter.
Surface devices missing required endpoint agents with a simple, policy-aligned query.
Want to narrow it further? Add additional filters like:
Only devices seen in the last X days
Only devices that are deemed critical or high value
Specific subnets, VLANs, or business units
Step 3: Detect endpoint agents that aren’t functioning
An installed agent doesn’t always mean a functioning one. Users disable agents. Devices go unmanaged. Tools silently fail. To catch these cases, Axonius lets you compare activity across data sources. For example:
Query:
Device has a CrowdStrike Agent ID
CrowdStrike “last seen” date is older than 30 days
But the same device has been seen by AD (or another system) within the past 7 days
This tells you the device is active on the network, but the agent hasn’t checked in, meaning it’s likely disabled, broken, or removed.
.png)
This query identifies devices where the CrowdStrike agent hasn’t checked in recently, but the device is still active in another system, indicating a likely failure or uninstall.
This is the kind of query that’s nearly impossible to build without a cross-correlated dataset, and it’s one of the most valuable for catching silent failures.
Step 4: Take action at scale
Once you’ve identified devices with missing or nonfunctioning agents, you can respond directly from Axonius using the Enforcement Center.
Popular enforcement actions include:
Deploy the missing agent (e.g., install the agent using tools like SCCM or Tanium)
Notify the right team or owner via email, Slack, or Syslog
Open a ticket in tools like ServiceNow, Jira, or Zendesk
Run a command or initiate an SSH scan
.png)
After identifying devices missing an endpoint agent, you can use the Enforcement Center to determine the appropriate automated action.
You can even schedule these queries to run continuously and trigger enforcement automatically, so you’re not relying on manual checks.
Example: Context-aware agent coverage
Let’s say your environment uses:
CrowdStrike for some devices
Microsoft Defender for other devices
You can segment your queries accordingly:
No CrowdStrike AND No Defender = Noncompliant
CrowdStrike OR Defender Installed = Compliant
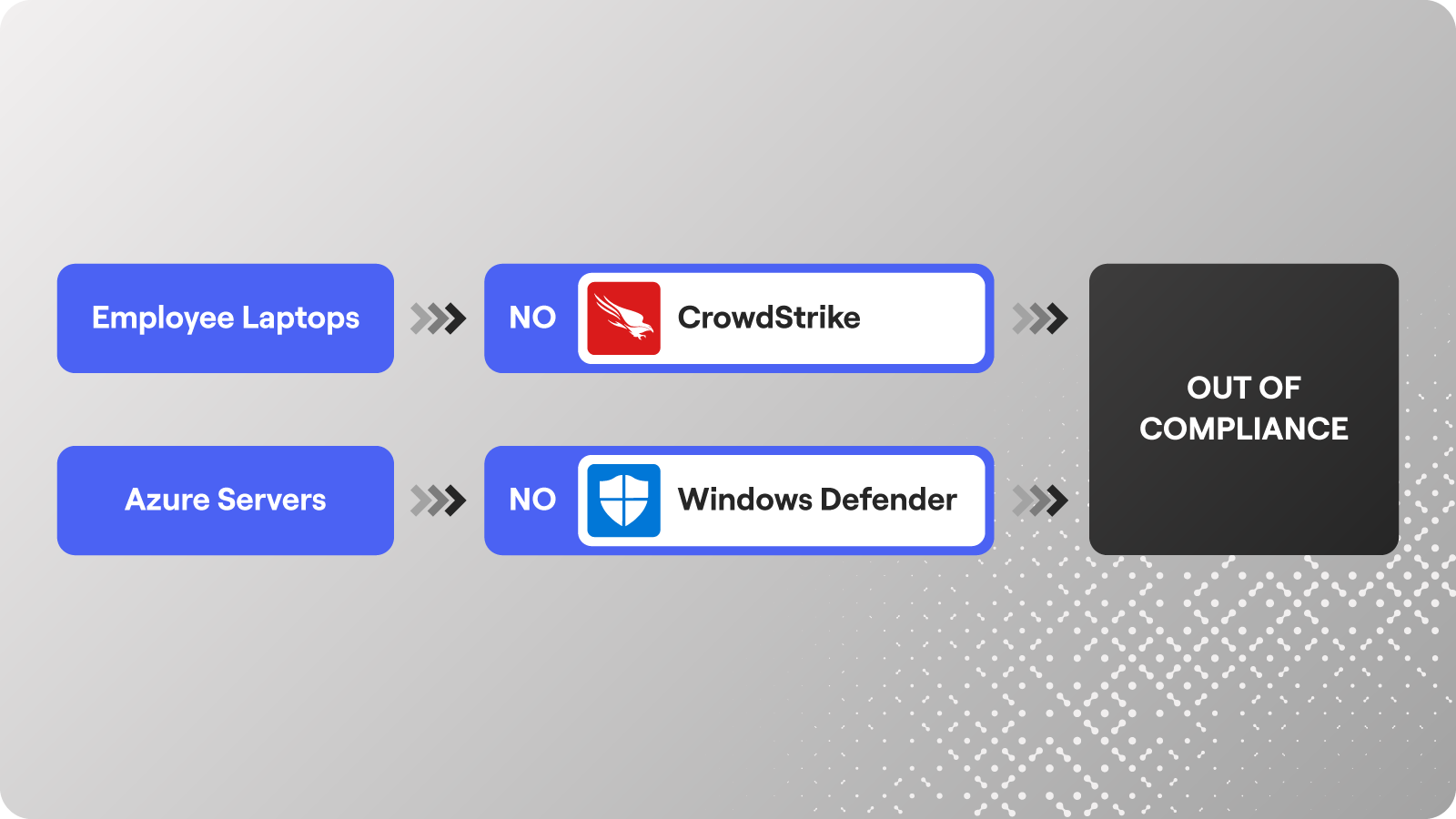
Segment assets by type and required agent to identify systems that fall out of compliance based on real-world policy logic.
This kind of policy-aware query structure helps you enforce controls based on real-world context, not just one-size-fits-all lists.
Fix the gaps in your endpoint protection today
You already have the data; Axonius helps you make sense of it and take action.
Spot the gaps. Surface the devices that are missing agents or running ones that aren't working. Then fix them at scale, automatically. No exports, no VLOOKUPs, and no guesswork.
Get a product demo or speak with a representative today and learn how Axonius can help you tackle threat exposures, misconfigurations, and operational inefficiencies all in one place.
Categories
- Endpoint and IoT Security
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
