Beyond the vault: Why PAM and IGA are stronger together

Julissa Caraballo
Principal Product Marketing Manager, Axonius
.png?width=3440&auto=avif&format=jpg&disable=upscale)
Palo Alto Networks' recent acquisition of CyberArk underscores a growing reality in the identity and security space: Privileged Access Management (PAM) can no longer operate in isolation. The convergence of network security, identity governance, and privileged access is accelerating, and enterprises are rethinking their architecture for enforcing least privilege and operational control.
While PAM has long been a cornerstone of enterprise security, controlling, vaulting, and auditing access to high-risk accounts, its effectiveness depends entirely on the quality of the data feeding into it. PAM can control what it knows. But it can’t protect what it can’t see. And that’s where identity governance becomes essential.
At Axonius, we understand that PAM and Identity Governance and Administration (IGA) aren’t competing categories. They’re complementary functions, mutually dependent, yet often disconnected in practice.
Our approach with Axonius Identities is designed to bridge this gap. That means you finally have a unified, real-time picture of who has elevated access, where, and why, no matter where that access resides.
The governance gap inside PAM
PAM excels at controlling access to privileged credentials that are explicitly onboarded: root accounts, domain admins, service accounts, and more. It handles vaulting, session recording, credential rotation, and just-in-time access controls.
But PAM doesn’t tell you which accounts should be managed. It assumes you’ve already done that work. That assumption is where many organizations stumble.
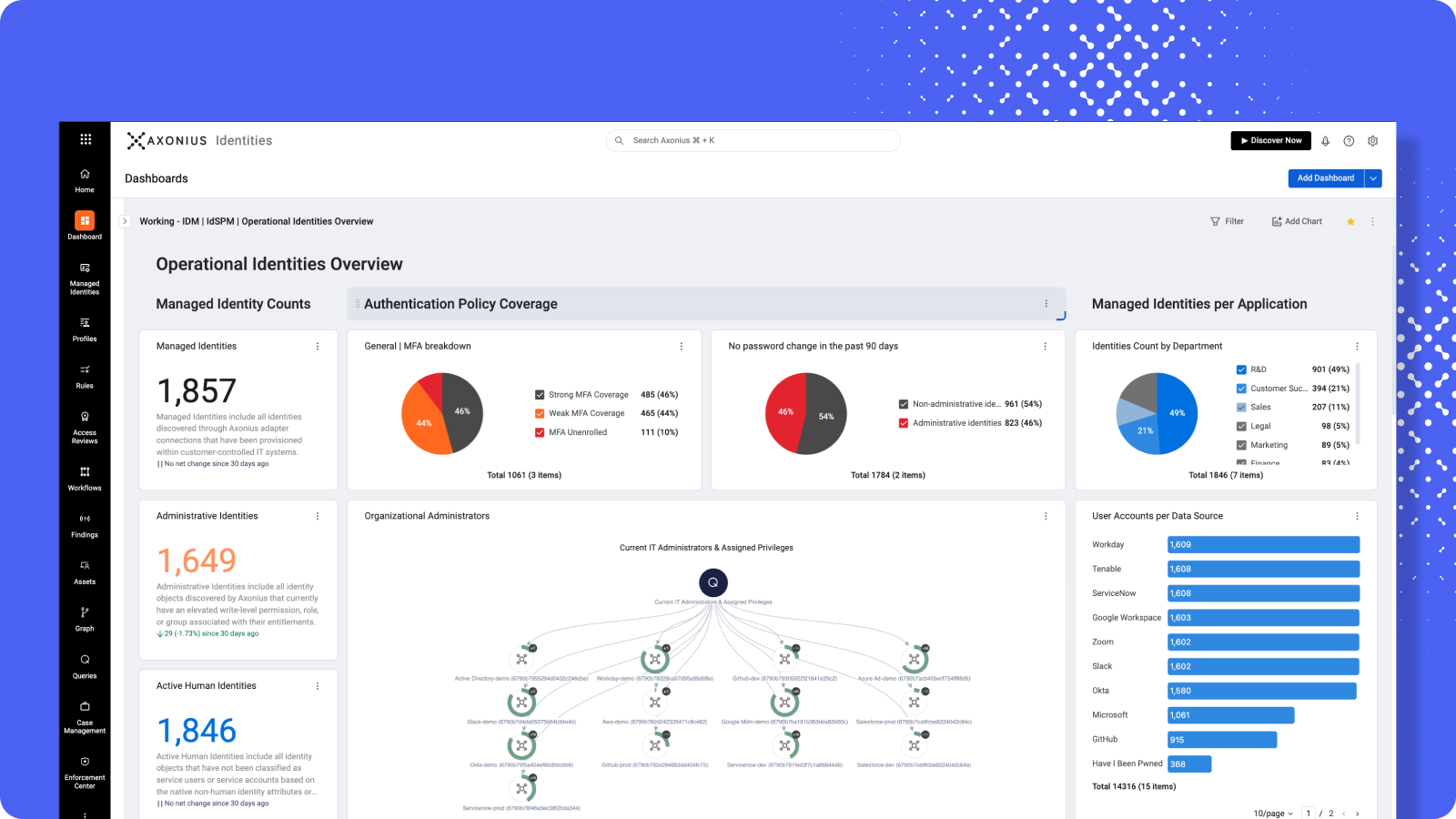
With Axonius Identities, you get a real-time view of who has elevated access, where, and whether it aligns with policy. Close the gaps PAM can’t see.
Most PAM deployments rely on static onboarding processes, spreadsheets, or IT requests to define what “privileged” means. In reality, elevated access is everywhere: in cloud roles, SaaS admin panels, on-prem apps, and local machines.
Many accounts with critical privileges are never onboarded into PAM at all, either because they were missed, misclassified, or provisioned outside of formal workflows.
That’s not a fault of PAM. It’s a fault of the surrounding identity data infrastructure. PAM is only as good as the governance and discovery process upstream from it.
Why PAM needs IGA, and vice versa
Traditional IGA tools were supposed to solve this problem by centralizing identity and entitlement data, providing workflows for access certification, and ensuring least privilege through policy. But legacy IGA often suffers from slow time-to-value, fragmented data, and limited context into modern SaaS and cloud environments.
On their own, PAM and IGA both do important things. But together, they can close the loop between discovery, governance, enforcement, and remediation.
Here’s what that looks like in practice:
Stay ahead of privilege sprawl. Axonius continuously discovers users and accounts with elevated access across all identity systems, whether or not they’re onboarded into PAM.
See everything, everywhere. We build a correlated identity graph that unifies human and non-human identities across IdPs, IAM tools, SaaS platforms, cloud providers, and infrastructure.
Take action with confidence. We validate whether elevated access aligns with policy, highlighting hygiene gaps like missing MFA, remote login enabled for Domain Admins, or interactive logins allowed for service accounts.
Eliminate risk without the manual work. We automate cleanup workflows, detecting dormant or stale privileged accounts and triggering offboarding or deactivation.
Make onboarding faster and more informed. We enrich PAM onboarding processes by feeding in newly discovered admins, complete with department, owner, usage history, and peer context.
Start with the full picture, not just what you already know. Axonius makes sure your PAM program begins with complete context.
A real-world example: Closing the loop
Imagine an enterprise using CyberArk to manage its privileged credentials. On paper, their PAM program looks mature, vaulting is enforced, sessions are recorded, and password rotation happens on schedule.
But behind the scenes:
A handful of AWS accounts with administrative access were never onboarded into CyberArk.
Several local admin accounts exist on legacy servers outside of Active Directory.
A SaaS application admin was granted elevated access directly through the app’s UI, bypassing IT request processes.
A service account is misconfigured to allow RDP logins, and no one notices.
PAM is doing its job, but it’s not seeing the full attack surface. With Axonius, you can uncover each of these blind spots, tie them back to identity owners, and easily route them into CyberArk for onboarding or cleanup.
This isn’t just theoretical. Across our customers, we’ve consistently found that even the most well-governed PAM environments still miss 15–25% of privileged accounts, simply because they weren’t known in the first place.
Getting more from the investments you’ve already made
Organizations have spent years and millions of dollars deploying PAM and IGA solutions. But those investments are often undercut by poor visibility, siloed data, and fragmented enforcement.
Rather than replace these systems, Axonius ensures they operate with complete and accurate data, so the controls you’ve already put in place actually work as intended.
When PAM and IGA operate from a shared, continuously updated view of identity and access, you can:
Detect toxic combinations of access in real time, before they’re exploited
Offboard privileged users cleanly and completely, no matter where they hold access
Prove enforcement with real-time evidence for audits and compliance
Prioritize remediation efforts based on identity risk and usage context
The future of privileged access is converged
The CyberArk-Venafi acquisition is just one example of a broader shift toward identity convergence. As organizations embrace Zero Trust, consolidate identity platforms, and move toward real-time enforcement, the lines between governance, access control, and security are blurring.
We believe the next generation of identity security will be built on a foundation of correlated, normalized, and continuously validated identity data.
PAM will remain essential. But to make it resilient, scalable, and effective, we need governance to be continuous, not quarterly. We need discovery to be automated, not spreadsheet-driven. And we need identity security to be unified, not stitched together through manual effort.
By turning privileged access from a set of assumptions into a set of facts, Axonius Identities helps your existing investments in PAM go further than they ever could alone.
To learn more about Axonius Identities, schedule a demo with our team today.
Categories
- Identity
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
