Security teams are ready to act. Dirty data is slowing them down.

On paper, you're ready. 90% of security and IT leaders say their organizations are prepared to respond when a critical vulnerability hits.
But when it actually happens, things can quickly start to unravel. Patches roll out slower than expected. Conflicting data causes confusion. Prioritization gets messy.
Why does this happen? And why does it keep happening across even the most experienced, well-resourced teams?
To find out, we commissioned The Trust Factor: How Trusted Data Drives Smarter Vulnerability and Exposure Management, a research study of 500 security and IT leaders.
What we uncovered confirms what many teams have long suspected: readiness doesn’t mean much if you can’t trust the data behind your decisions.
Only 25% of leaders say they fully trust the security data in their tools. Grappling with that “dirty data” is where execution starts to fall apart. |
Why security feels so reactive (even when you’re “ready”)
Security teams are flooded with data from all angles. But more data doesn’t mean better security if that data is inconsistent, incomplete, or just plain wrong.
Our survey found the primary sources of mistrust. Here’s how security leaders rank the biggest blockers to trusting their data.

What does that look like in practice?
Inconsistent data: Two tools flag the same vulnerability with wildly different scores. Which one do you believe?
Incomplete data: Entire categories of assets are missing, so exposures go undetected until it’s too late.
Inaccurate data: Outdated or incorrect information leads your team down the wrong path.
The high price of low trust
This trust gap directly impacts your organization’s risk exposure.
81% of organizations take more than 24 hours to remediate a critical vulnerability. Only about three in ten organizations conduct vulnerability (29%) and exposure (28%) assessments weekly or daily. |
That means:
Critical vulnerabilities linger for longer than they should.
Security teams waste time chasing down conflicting or outdated information.
Even AI and automation tools fall short, because if the data is bad, the output is, too.
How do you close the trust gap?
Security and IT leaders know what they need, and it’s not more tools or more data. It’s better data and better ways to act on it.
Nearly a third of respondents (29%) say risk assessment and prioritization is still a challenge. And 27% say integrating data across tools is holding them back. |
We asked security leaders what would help provide more actionable insights into vulnerabilities. Here’s what they said.
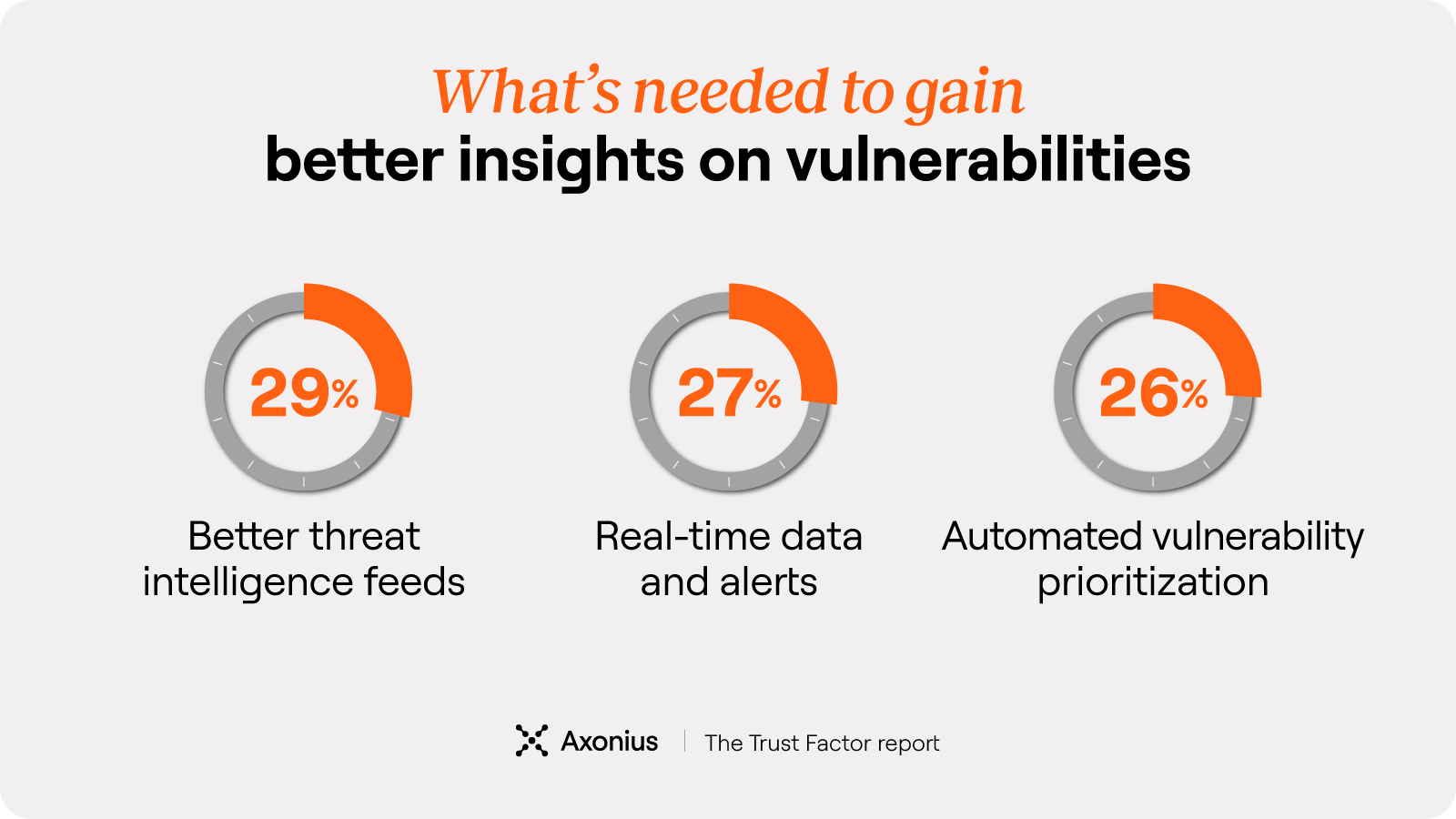
Even with more data and tools than ever, gaps in threat management still persist. What teams really need is a strong data foundation. The kind that powers timely alerts, smarter prioritization, and threat intelligence that actually drives action.
Turn confidence into real execution
Everyone wants to be proactive. But you can’t move fast or make the right call if your data isn’t reliable. When your view is incomplete, your response will be, too.
It all comes down to investing in the foundation your tools depend on: trusted, connected data.
Grab the full report for deeper insights and actionable takeaways to help your team turn readiness into real results.
Categories
- Threats & Vulnerabilities
Get Started
Discover what’s achievable with a product demo, or talk to an Axonius representative.
